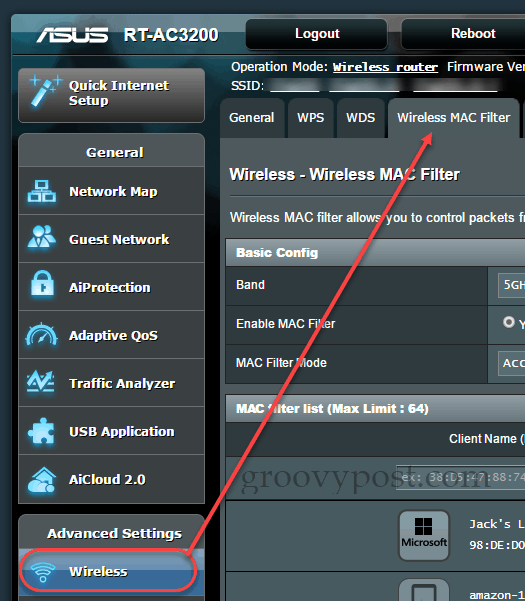
MAC Filtering ASUS Router
If it talks on your network, wireless networks included, it has a unique MAC address that never changes. On an ASUS router, you have two options for using MAC filtering.
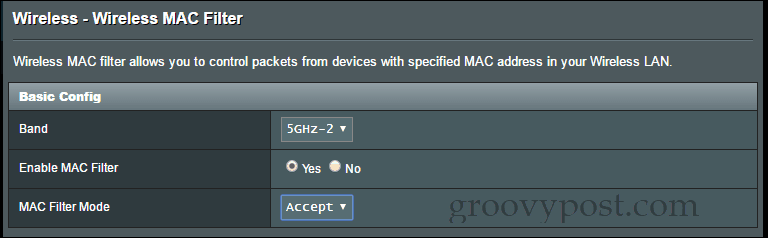
Accept mode is a whitelist. You specify which devices are allowed to connect. Everyone else is blocked.Reject mode is a blacklist. You specify which devices are not allowed to connect. Everyone else can use the network.
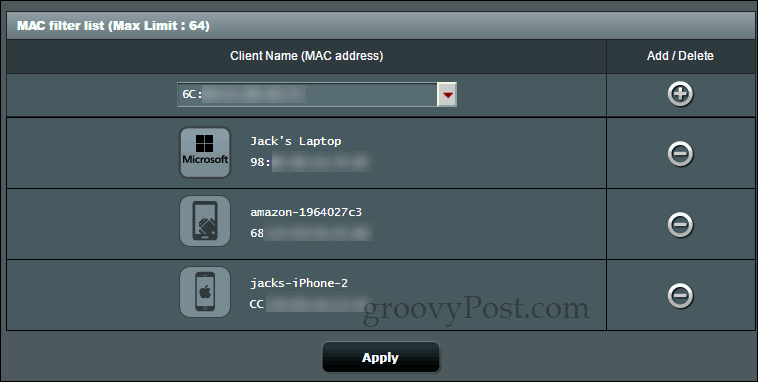
A whitelist is the most secure, but it requires more hands-on management, and you need to have a comprehensive tally of all the devices that connect to your wireless router. If you forget something—a Blu-ray player, a thermostat, or a webcam, for example—then it won’t work. If it’s been a while since you configured your MAC filtering whitelist and you’re having trouble with a new device, it’s easy to forget the extra step of adding the new MAC address to your filtering rules. Personally, I recommend a whitelist for a separate band that you set up for kids or frequent visitors. This can be used instead of or in addition to a wireless guest network. I’m not sure what you’d use a blacklist for that you can’t also do with a password from a security standpoint. For parental controls, a blacklist can help you allow internet access on a laptop but not on a gaming console, I guess?
Steps for MAC Filtering
Here’s what you do to set up either wireless MAC filtering in accept mode or reject mode on an Asus Router. That’s all! Now, if you chose to use accept mode, only the devices you specified will connect. If you used reject mode, then the devices you specified will be blocked. If you try to connect to the network from a filtered device, it simply won’t work. You won’t get any error messages or block warnings. How are you using MAC filtering on your router? Let us know in the comments. the use of mac address filtering as a security measure and or to stop people connecting to your wifi is outdated and incorrect the mac address of any devices connecting to the network is not encrypted and can simply be read and replicated / spoofed onto your own device and bingo you bypassed this none effective solution the use of wpa2 psk with AES encryption should always be used and if so will stop anyone who doesn’t have the passphrase from accessing the wifi , just don’t give the passphrase out to people you don’t want connecting to your network A whitelist approach is going to be the most secure for mac filtering. For someone to exploit it, they would have to spoof a mac address on the white list. It’s easy to scan a network and find all the mac addresses for connected devices, but it’s harder to pull off if you can’t connect to the network. While not foolproof, a mac address whitelist is far from useless. Comment Name * Email *
Δ Save my name and email and send me emails as new comments are made to this post.
![]()